Interested in learning how to become a cyber security auditor! Read on as you learn everything to get your security auditing career started!
What Is IT Security Auditing?
IT security auditing (aka “information security auditing”) involves evaluating an organization’s IT systems and processes to identify vulnerabilities, ensure compliance, and improve overall security.
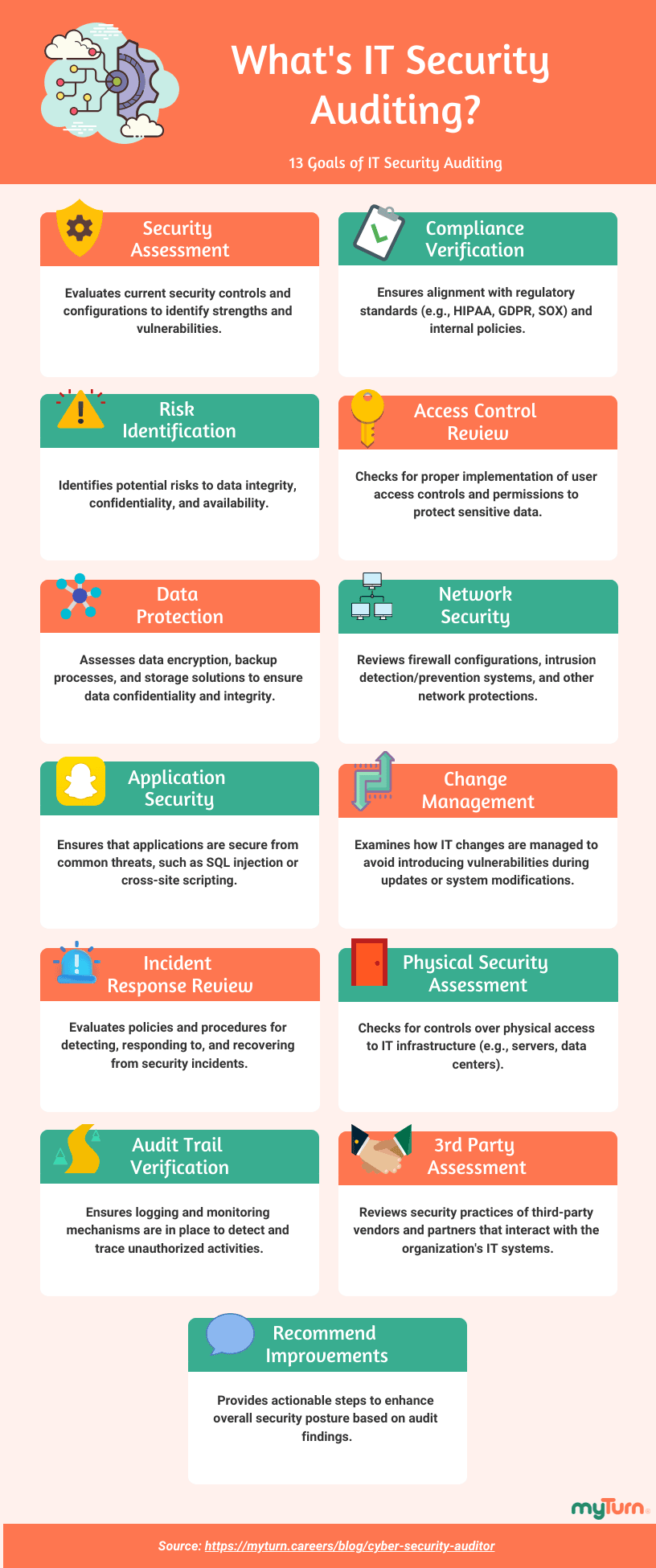
Here are 13 core aspects of cyber security auditing:
- Assessment of Security Posture
- Compliance Verification
- Risk Identification
- Access Control Review
- Data Protection
- Network Security Analysis
- Application Security Review
- Change Management Evaluation
- Incident Response Readiness
- Physical Security Assessment
- Audit Trail Verification
- Third-Party Security Assessment
- Recommendations for Improvement
What Is a Security Auditor?
A security auditor is responsible for evaluating and ensuring the effectiveness of an organization’s security measures. In other words, making sure the IT security audit is completed properly.
Let’s break down the specifics of their role in the next section.
Cyber Security Auditor Job Description
As I’ve previously mentioned, the role of security auditor is to ensure the organization’s data and information are properly safeguarded, but how do they go about doing that?
Cybersecurity auditors work with organization’s to:
- Assess Data Access Controls
- Evaluate Control Appropriateness
- Test Control Effectiveness
- Verify Compliance
- Conduct Risk Assessments
- Recommend Corrective Actions
- Report and Communicate
- Advise on Continuous Improvement
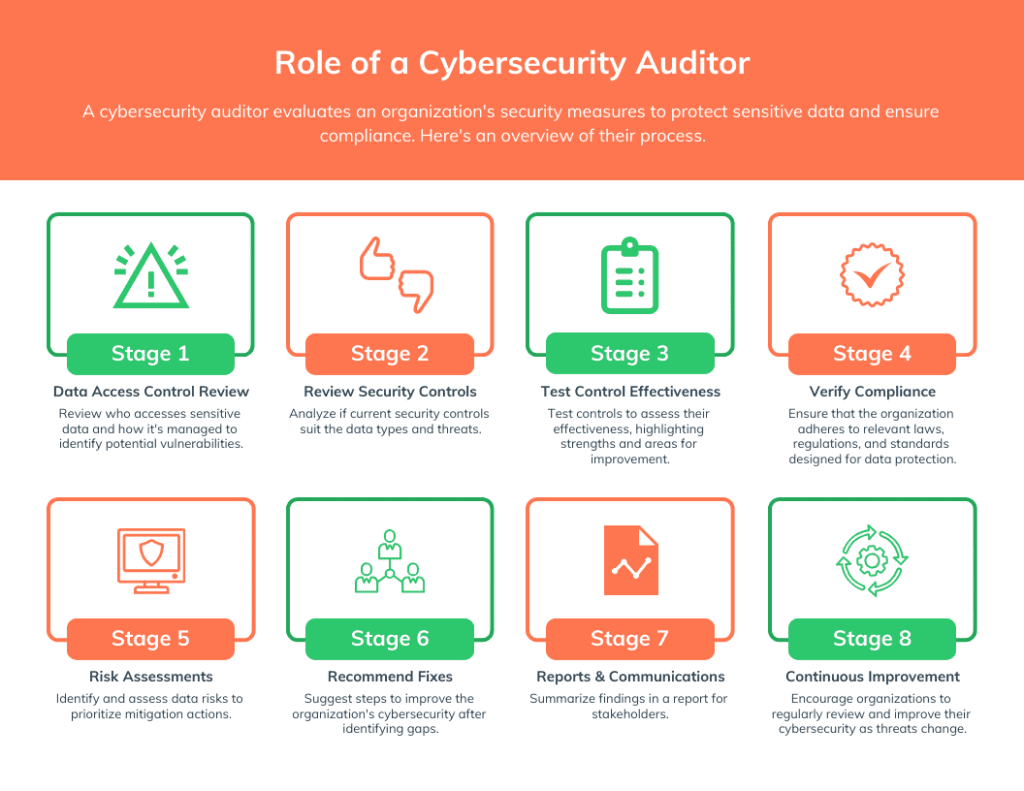
As you can see from the final stage, information security auditor roles and responsibilities are never-ending. It’s always a continuous loop of improvement.
Cyber Security Auditor Job Titles
Roles associated with a cyber security auditor may include:
- Information Security Auditor
- IT Security Auditor
- Security Risk and Compliance Auditor
- SOC (Security Operations Center) Auditor
- Governance, Risk, and Compliance (GRC) Auditor
- Network Security Auditor
- Cyber Auditor
- Physical Security Auditor
- AWS Security Auditor
- Cloud Security Auditor
- Blockchain Security Auditor
- Security Compliance Auditor
- ISO 27001 Auditor
And many more…
Cyber Security Auditor Salary
How much do auditors make? The average salary of a cyber security auditor is about $128k/year based on three sources:
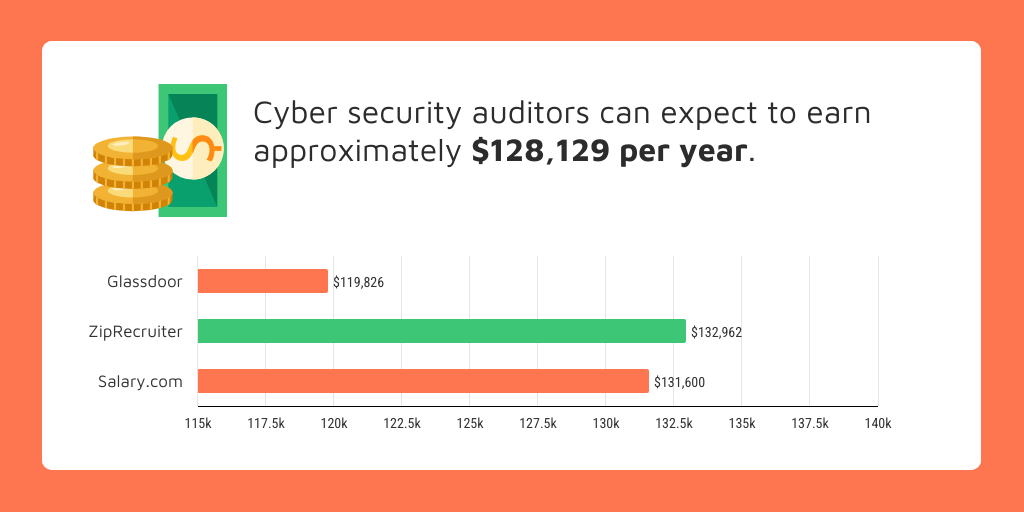
- Salary.com: Salary range falls between $94k to $153k and averages $132k
- ZipRecruiter: Salary range falls between $57k to $186k and averages $133k
- Glassdoor: Salary range falls between $78k to $194k and averages $120k
Based on this information, the pay of a cyber security auditor may range between $57k to $194k. Of course, this mostly depends on your education, location, and experience.
What Are Popular IT Security Audit Tools?
There are multiple cybersecurity audit and compliance tools you should use to provide reports for security audits.
Each tool serves a specific purpose within the information system. Here are some common cyber security audit tools:
- SIEM Tools (Security Information and Event Management)
- Code Scanning Tools
- Network Scanning Tools
- Vulnerability Scanning Tools
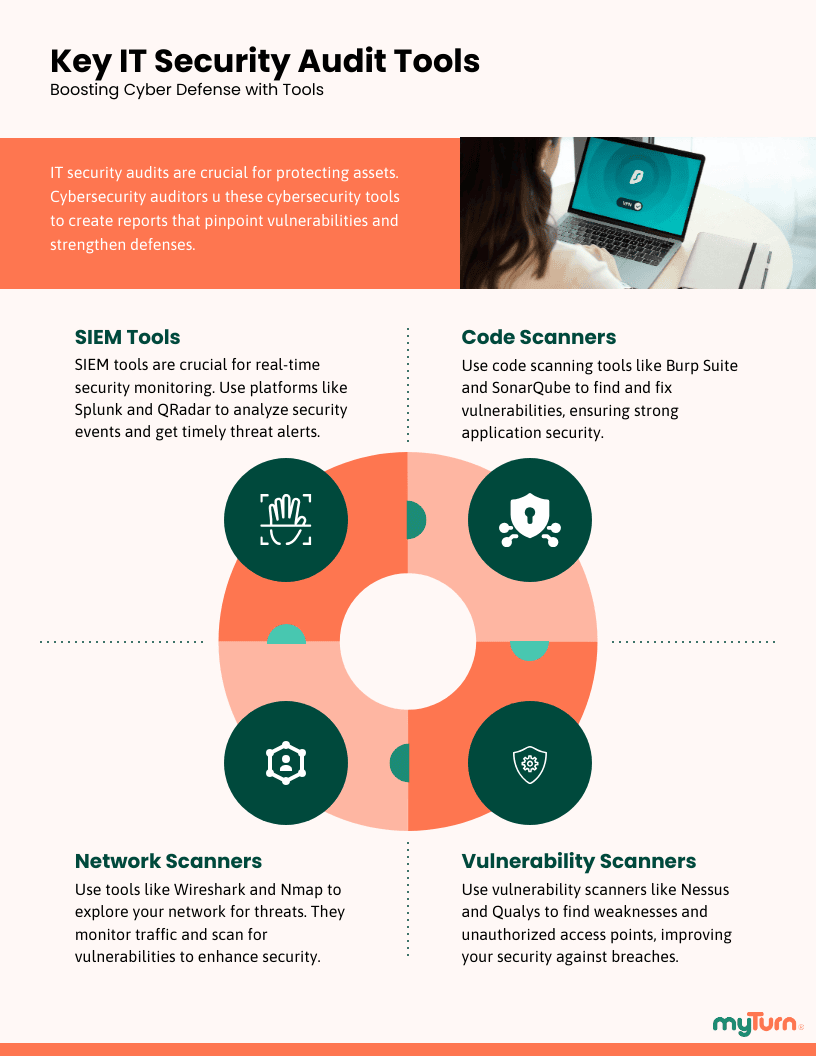
By leveraging a combination of these tools, you can build a comprehensive view of an organization’s security posture and make informed recommendations for improvement.
How to Become a Cyber Security Auditor?
If you’re truly interested in learning how to become an information security auditor, one of the best methods to get a job is to gain experience first.
Even if you don’t have a degree or any other certification, experience is an absolute must!
But if you’re having trouble finding a role, I’ve provided an alternative cyber security auditor career path to help you become an auditor.
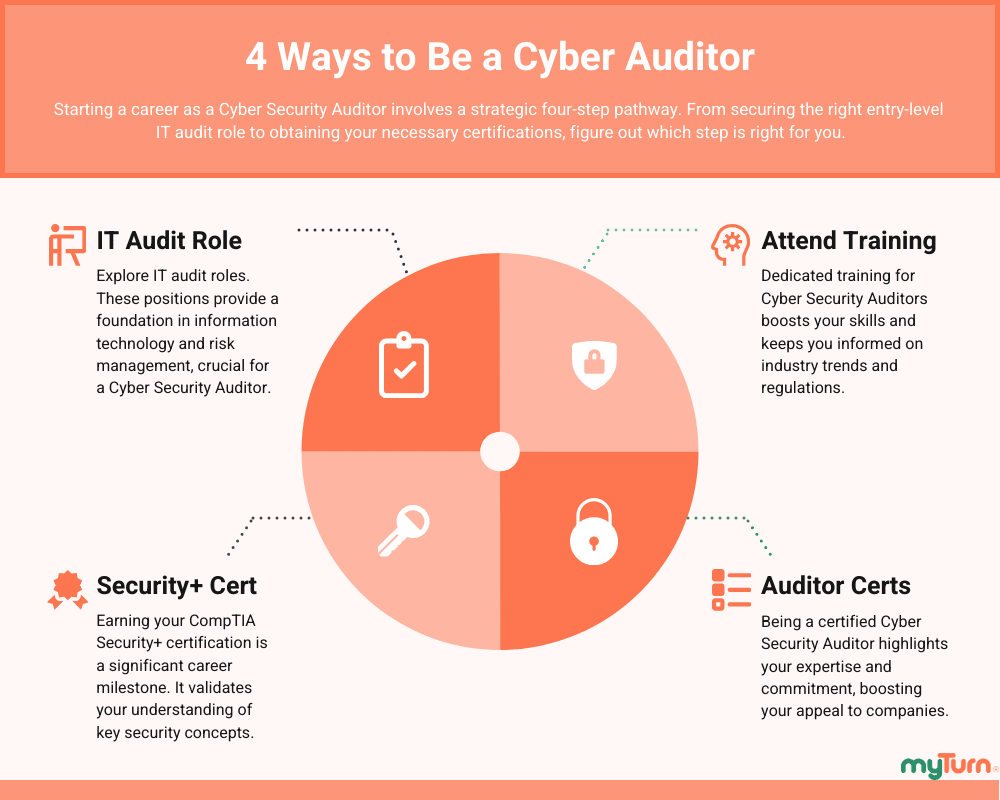
Apply for an IT Audit Role
If you can’t find a job as an information security auditor, then don’t waste too much time. As counter intuitive as it may seem, find a job working in IT auditing, not information security.
Is IT audit a good career? Yes, as an IT auditor, you’ll gain enough experience to pick up some security knowledge along the way.
And as an added benefit, there are more job opportunities as an IT auditor then there is audit in security.
Get Your Security+ Certification
Before you even think about moving into information security, you’ll need your very first certification, the CompTIA Security+.
The good thing about this certification is that it doesn’t require any experience and immediately gives you some infosec credibility.
Become a Certified Cyber Security Auditor
Once you’ve had sufficient experience as an IT auditor, you’ll want to make the move into information security and audit.
At this point, you’ll want to consider taking one of the following cyber security auditor certifications to appear more serious about your auditing career:
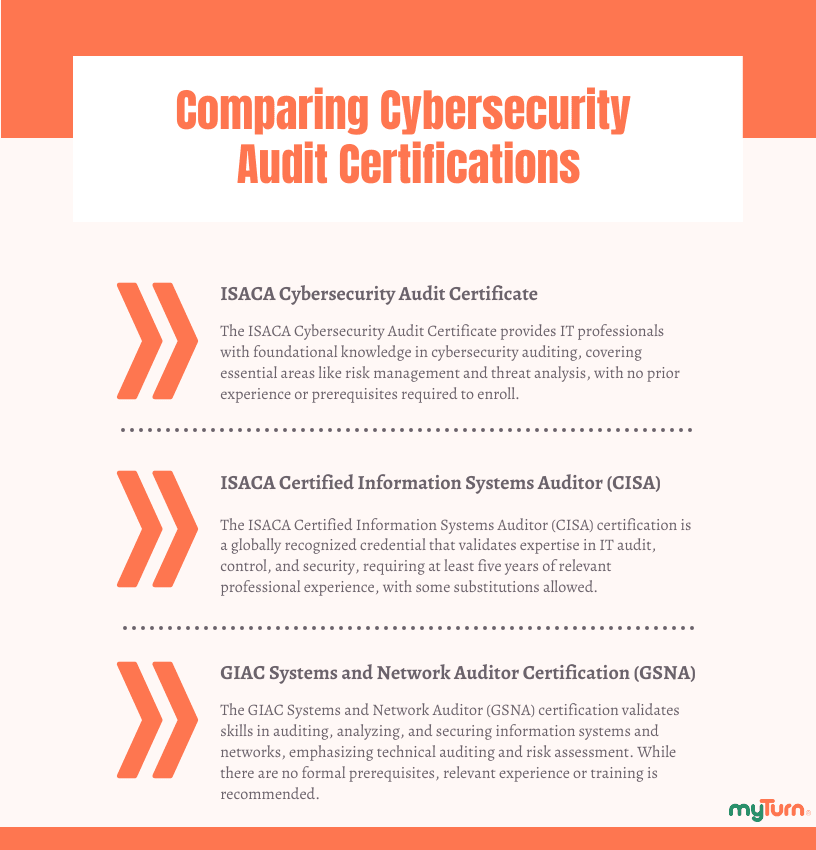
- ISACA Cybersecurity Audit Certificate
- ISACA Certified Information Systems Auditor (CISA)
- GIAC Systems and Network Auditor (GSNA)
Overall, these certifications provide a good path to becoming a certified information security auditor no matter what stage of your career you’re in.
Cyber Security Auditor Training
Though it’s not required, you might want to take a security audit course if you’re having trouble getting certified.
There you’ll be trained to understand the security aspect of auditing which may or may not be associated with any certification program.
Here are a few information security audit training programs to get you started in the right direction:
- Information Systems Audit and Control Association (ISACA)
- The SANS Institute
- The Institute of Internal Auditors (IIA)
- Information Security Management System (ISMS)
Regardless of your choice, as always, I recommend going with an officially authorized information security auditor training program; otherwise, find a program that’s been certified by an accredited body.
Cyber Security Auditor Skills
Let’s break down the skills needed for a cyber security auditor job into several categories.
Interpersonal Skills
While evaluating the company’s security posture, you’ll be working with multiple personnel, some of whom are used to doing things a different way. Unfortunately, your role is somewhat intrusive in nature which may not be appreciated by all those involved. As a result, having empathy is essential in your role, especially for those with limited resources or lack of knowledge in your area of expertise.
Technical Skills
Being technically savvy is part of the job. Information security is highly technical in nature, so you’ll need a deep understanding of how information systems operate as well as a solid understanding of how to interpret security audit tools.
Analytical Skills
Vital when performing your role as an auditor as you need to have a keen eye for details and be inquisitive. You’ll be required to gather and analyze information from various sources such as information systems; security documentation; personnel interviews; and security procedures, processes, and controls to understand where deficiencies are present.
Presentation Skills
Expect to present your findings to leadership regardless of the outcome. The ability to present usually requires a bit of finesse; you’ll be speaking to personnel that may not understand the technical language or might have difficulty in accepting your findings.
Patience
Conducting an audit takes a few weeks to several months. Leadership teams will expect you to provide them with continuous status updates. During that time, you’ll have an enormous amount of information from which to gather and process.
Information Systems Auditor vs Information Security Auditor
It’s important to understand that both job titles are not interchangeable. In general, there are many similarities between the two roles: both positions involve auditing computer systems for the purpose of ensuring accuracy and risk reduction. However, the key difference is the nature of their roles:
Information Systems Auditor (aka IT Auditor)
During an information systems audit, the auditor is concerned with the efficiency of the company’s information systems.
Information Security Auditor
During IT security auditing, the auditor is concerned with the security of the company’s information systems and not its efficiency.
Internal Security Auditor vs External Security Auditor
There are two types of security auditors, external and internal. Let’s look at both:
External Security Auditor
An external auditor is a third-party agent whose purpose is to validate a company’s compliance with a government or regulatory requirement.
Internal Security Auditor
An internal auditor is an employee or third-party consultant hired to perform audit functions to help the organization maintain compliance with an external audit.
For example, if a company wants to be ISO 27001 certified, they may hire an internal auditor to identify deficiencies in their IT policies, procedures, and controls, who then works with the company to bring them into compliance. The external auditor would then validate that the company has made the necessary adjustments to their information system practices to meet the requirements of ISO 27001 certification.
Compliance Standards for Security Auditors
When your company decides upon a cyber security framework, they might be required by law to follow a specific framework. For instance, medical facilities are required by law to follow the Health Insurance Portability and Accountability Act (HIPAA) dictating how personally identifiable information should be maintained by the healthcare industry.
While there are many frameworks or laws for which a company may follow, some of the more common ones are:
NIST Cyber Security Framework (CSF)
NIST Special Publication (SP) 800-53
CIS Critical Security Controls
As an auditor in the US, you’ll find that these four frameworks are worth learning. To make it easier, you’ll find some overlap between them.
Interested in More…
Wondering How to Be a SOC Analyst?
Choose the Right Career, Cyber Security vs Ethical Hacking
Cyber Security vs Data Science: Which Is Better?
Difference Between Cyber Security vs Cloud Security



