Cybersecurity Recruiters…you’ve heard the myths, and you’ve seen the daunting job descriptions.
You’re probably thinking that your resume is a perfect fit for the job and there’s no reason to change it.
So, you apply and apply thinking that it should be any day now. Those recruiters are gonna be falling all over to get you hired.
Then a few days go by, and you don’t hear anything back. You start applying to other places, and yet you still don’t hear anything back.
Your friends and colleagues are getting interviews, but you’re still wondering when your turn’s coming up.
After a while, you start getting frustrated. There’s no doubt in your mind that every cybersecurity recruiter is passing up on your resume.
After a while you start to think you’re not good enough!
The reality is, you’re not alone in situation; there’s probably thousands of candidates in this same position.
The BLS actually posts this data and defines this as being a “discouraged” individual.
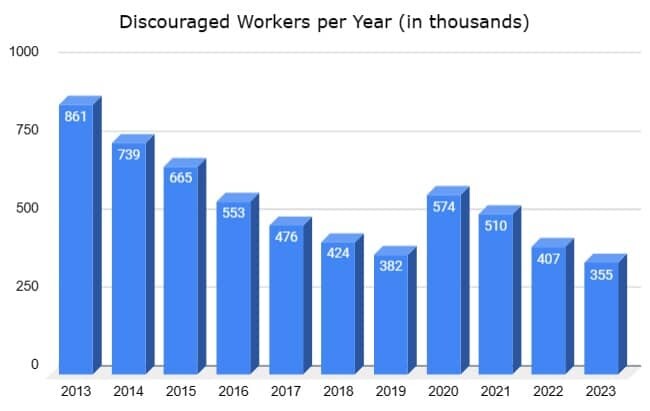
Yet, how do you make yourself stand out? How do you understand what recruiters really want from a cybersecurity candidate?
Let’s unravel these questions together.
11 Reasons Why a Cybersecurity Recruiter Will Trash Your Resume in a Heartbeat!
First thing’s first…is your resume getting trashed?
When you write a resume, it better be written to sheer perfection. You don’t have a lot of time to impress a recruiter.
Granted, I’m sure there are a few recruiters that are slightly forgiving if you have the best qualifications for the job, but I wouldn’t hold my breath.
Why is that so? Recruiters equate less-than-perfect resumes with less-than-perfect performance. And no company can afford that.
A survey of 946 hiring managers, HR professionals, and workers across multiple industries were asked about common resume mistakes that would lead them to trash a resume, here’s what they indicated:
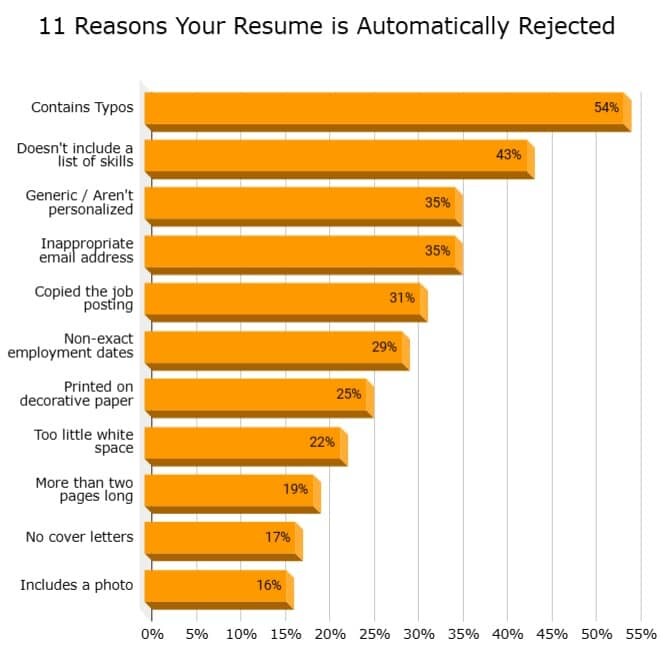
The message is clear, before you keep applying endlessly, make sure you’ve taken the time to go through your resume. Figure out if you’re doing something wrong.
Tailor Your Resume for Cybersecurity Job
Covering #3 on that list of reasons, your resume is often the first impression cybersecurity recruiters have of you. The problem with many resumes is that your so called “perfect resume” isn’t tailored to the position you’re applying for.
Unlike other fields, each role in cybersecurity can be unique, requiring specific skills and experiences.
Tailoring your resume to match the job description isn’t just advisable; it’s essential. Take your experience and make it work for you.
Using online templates and tools specific to cybersecurity can ensure that you’re highlighting the right aspects of your experience.
Take a look at the Cyber Career Pathways Tool video below developed by NICCS to help you determine if you’ve included the right knowledge, skills, and abilities that are common for your role. (The video’s a bit dry, but it’s short and a good starting point.)
Consider seeking professional resume reviews to present the best version of yourself.
Your resume shouldn’t just be a list of your past roles and achievements; it should tell a story.
It should convey your passion, your expertise, and your readiness to take on the challenges of the role.
In crafting a resume that resonates with cybersecurity recruiters, you pave the way for them to see you not just as a candidate, but as a future key player in their organization.
Cybersecurity Recruiters Can’t Agree on How Many Pages Your Resume Should Be
This is probably one of the most asked questions in the history of job applications. The answer to that question really depends on your geographic location and job culture.
In some countries, companies require an extraordinary “CV” detailing every aspect of what seems like your entire life. Luckily, in the US, you only need to list information that’s relevant to the role you’re applying for.
I will say that for entry level candidates, a page to a page and a half is good enough to get your knowledge and experience down. This should take into account your experience as a cashier, electrician, teacher…you get the idea (your non-cyber experience).
But, just to give you a sense of how confusing it can get for entry level candidates…
Zety, the Resume Builder site, published two separate articles: one showing that 66% of employers prefer candidates to have one page, and another where they found that two-page resumes were 1.4x more likely to get picked by recruiters.
I’m sure Zety’s a great company but not even the experts can always agree. Ultimately, do what’s right for your situation, and only write down what’s relevant for the role you’re applying for! Sorry…no one cares about your lemonade stand from when you were eight.
How Long Do Cybersecurity Recruiters Spend on My Resume?
The answer is not long. But, each recruiter is different which means they each look for different things on your resume.
Of course, this is dependent on each company.
If you’re applying to Google, don’t expect their recruiters to spend a lot of time on your resume. In fact, Kyle Ewing, Director of Recruiting at Google, even commented that her team of recruiters spend no more than 6-seconds on a resume. Not surprising when you get 3 million resumes a year!
The reality for most of you is better but not by much. According to a 2018 study conducted by Ladders, the average recruiter will spend about 7.4 seconds per resume to initially screen a resume.
Check out this heatmap to give you an idea of where recruiters spend most of their time looking…

Not Every Cybersecurity Recruiter Uses an ATS to Filter Your Resume
Despite what you’ve been told for so many years, not all companies use Applicant Tracking Systems. Not even the almighty Google uses an ATS, they screen every resume by hand.
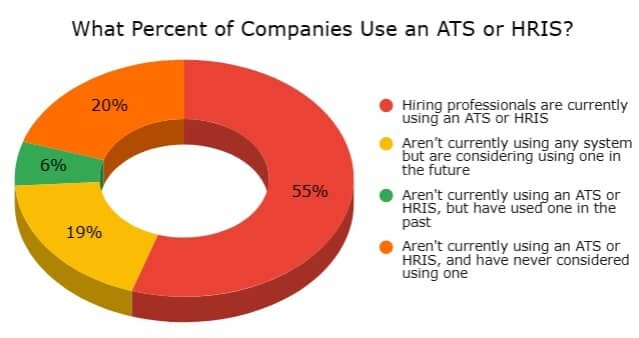
That’s right, that means 55% of companies are using an ATS/HRIS including the 99% of the Fortune 500. That also means the other 45% aren’t using an ATS!
So, while you do have to tailor your resume for an ATS, you no longer have the luxury of saying, “the ATS screened out my resume” when nearly half of companies don’t use them!
If you’re resume passes the recruiter’s initial screening, then you’re in luck as he or she is willing to spend a couple of extra minutes going through the details.
So, it’s really important that your resume highlights the details to make sure you catch their attention fast! Did you lead a project? Implement a critical security measure? Make sure those accomplishments stand out.
Cybersecurity Recruiters Hate It When You Make Their Job Harder!
If you’ve never worked in the HR space, you’re probably not expected to know this. Recruiters in general hate it when you waste their time.
Here are several things to keep note of:
Immigration Status
This is important within the cybersecurity space where employers either prefer (or require) US based employees. Now even though it’s illegal for employers to ask the specifics of your immigration status, it might be best if you go ahead and list it anyways. This is especially true if you’re a Green Card Holder, US Citizen or even have a clearance (when applying to government jobs). If you don’t have those but are still allowed to work in the US, at least write “Authorized to Work in the US”. Not writing anything may raise suspicion and lead to your resume being rejected.
File Names
When sending your resume, whether by email or web upload, your filename should never be “My Resume.exe” or anything so vague. Companies deal with hundreds of resumes a day. Could you imagine if every resume in their folder list started out with the same generic name, “My Resume”? Don’t assume that everyone remembers your resume. Renana Friedlich, Google’s Senior Director and Global Head of Cyber Threat Management, mentions that because she deals with so many resumes “your filename matters a lot!…It’s challenging…help me connect the dots“!
Don’t Lie
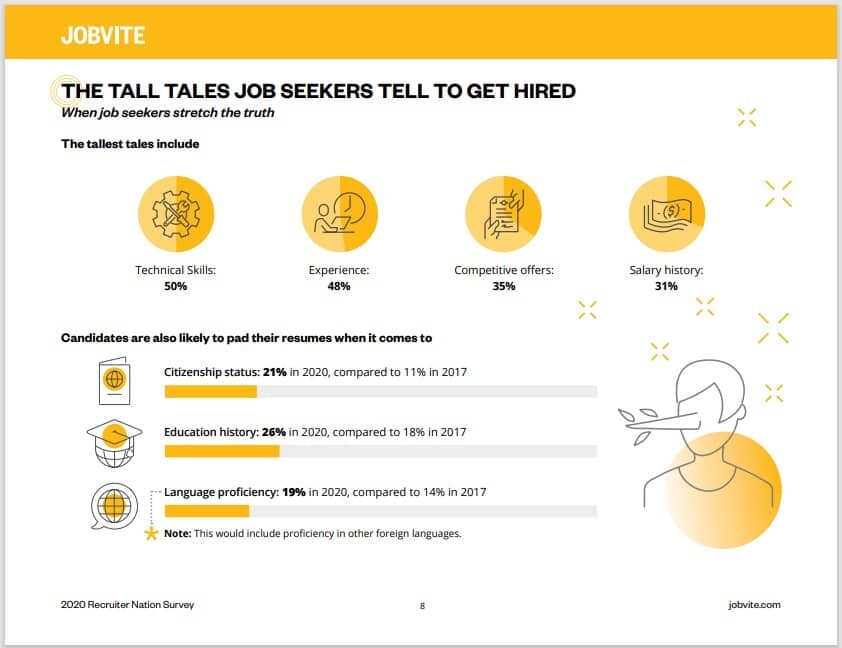
Flat out, lying will get you banned for life from that company. Or at least you can’t reapply there for several years. Everybody embellishes a little bit; instead, try to focus on your strengths instead of making yourself look better. Lying has gotten so bad, that one CareerBuilder survey found that 75% of employers have caught a lie on a resume.
Take a look at some of the most common lies that job seekers tell about themselves…
The Ever-Changing Landscape of Cybersecurity
The skills cybersecurity recruiters hunt for are never static; rather, they’re in a constant state of flux.
Employers want to know that you’re not merely keeping up with technology, but actively striving to be one step ahead.
To do this, you’ve got to immerse yourself in a state of continuous learning.
Show recruiters that you’re you try to keep up to date with the latest trends in the industry.
Ensure your resume lists conferences, workshops, training sessions you’ve attended — anything showing you’re attempting to grow.
If you’re having trouble, use sites such as Meetup, EventBrite, BSides, or InfoSec Conferences to find events that you can attend. And those are just the tip of the iceberg.
There are so many cybersecurity clubs, job fairs, conferences, and organizations you can attend, there’s no excuse not to!
The Power of Networking
There’s also another maybe not so obvious reason to attend the events I previously mentioned…networking!
Your network is more than a collection of contacts; it can open doors to opportunities that would otherwise remain closed.
Engaging in community events, networking with peers, and maintaining an active online presence lets cybersecurity recruiters know that you’re actively committed to the industry.
There’s no doubt platforms like LinkedIn and Twitter are tools in narrating your professional journey, but networking goes beyond just online interaction.
Regularly engaging with professionals in the field fosters connections that could lead to your next big opportunity.
The stories and experiences you share with others, and the relationships you cultivate, play an essential role in defining your career path.
Remember this, networking isn’t just about reaching out; it’s about connecting, understanding, and growing within the cybersecurity community.
How Cybersecurity Recruiters Look at Certifications and Education
Because you don’t have the experience, your certifications and education are the two most important pieces of information on your resume.
Regardless, your educational background, whether it’s a formal degree or self-taught expertise, contributes to your appeal as a candidate.
Similarly, certifications such as the A+, Network+, and CompTIA Security+ aren’t just acronyms; these credentials signal to cybersecurity recruiters that you have the specialized knowledge needed to excel in the field.
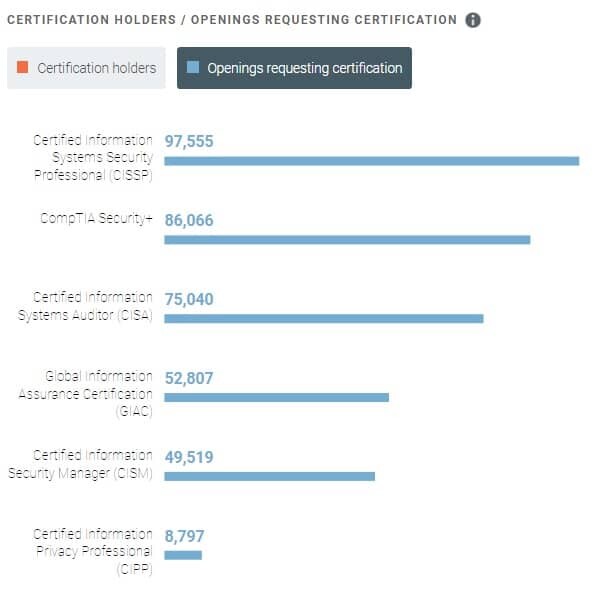
Just looking at the figure alone, that equates to roughly 370,000 open positions that are requesting certifications!
But don’t it wrong, it’s not just about collecting badges. The certifications you pursue should align with your career goals and the specific areas of cybersecurity that you’re passionate about.
Show that you are committed to growth, both through formal certifications and ongoing education, and you’ll stand out in the cybersecurity recruiter’s eyes.
Many platforms, such as Coursera or LinkedIn Learning, offer courses that can help you build a strong knowledge base. You can even access LinkedIn Learning through your library without having to pay dime!
The Skillset That Makes You Stand Out to a Cybersecurity Recruiter
Being technically proficient in cybersecurity is crucial, but cybersecurity recruiting is about hunting for more.
Recruiters seek candidates who can translate complex technical knowledge into something a non-technical team can grasp.
So, it’s important that you know how to strike a balance between your technical know-how and your ability to function within a diverse team.
That means cyber recruiters definitely prize soft skills like communication, teamwork, and adaptability in the workplace.
Engaging in collaborative projects, participating in hackathons, or taking public speaking courses can help you hone these soft skills.
For instance, signing up for Toastmasters is one of the best ways to brush up on your communication skills.
In demonstrating that you’re not only a technical wizard but also a collaborative team player, you make yourself a more desirable candidate.
The Interview – What Really Happens
The interview stage in cybersecurity is more than just a Q&A session; it’s a comprehensive showcase of who you are and what you bring to the table.
Recruiters expect candidates to understand the typical structure of cybersecurity roles, prepare for technical tests, answer behavioral questions, and solve real-world problems.
Questions like “What’s your approach to threat analysis?” or “Tell me about a project where you implemented a security solution” are designed to test your on-the-spot thinking and problem-solving abilities.
Preparing for these questions with confidence requires a deep understanding of the role and the company’s culture.
Research the organization’s recent news, key players, and overall mission. One of the best places you can start is by checking out Crunchbase. Here’s an example of my company with some of the detail listed…
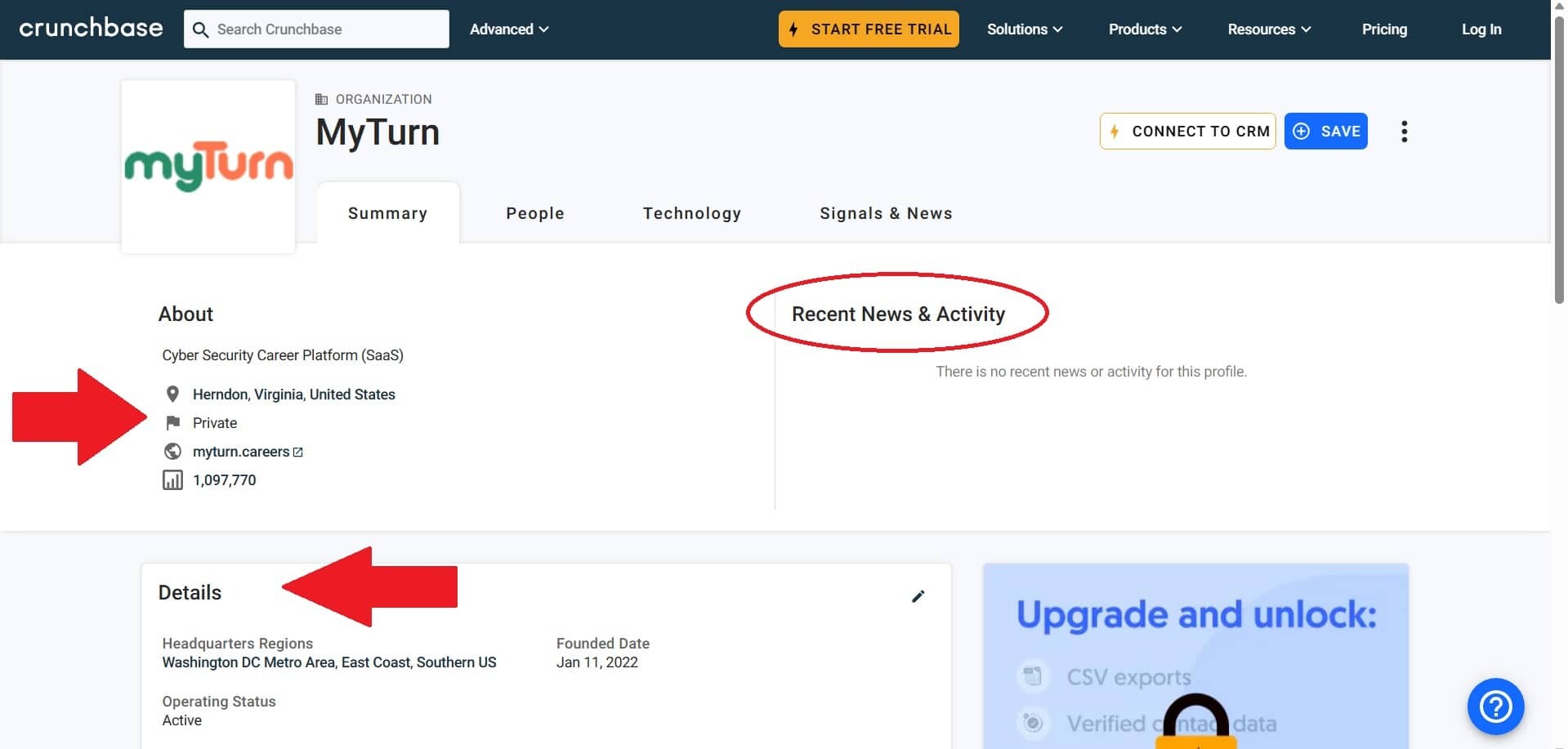
Tailor your answers to align with their values and show that you’ve done your homework.
The interview isn’t just about what you know; it’s about how you fit within the organization and how you convey your alignment with their goals.
Remember, it’s about presenting yourself as an asset, ready to contribute and grow within their ecosystem.
Personal Branding in Cybersecurity Recruitment
In the field of cybersecurity, your personal brand can make or break your chances with a cybersecurity recruiter.
Let’s take an example by looking at the difference between these two profiles, which would you be more interested by:
Or this one…
To be fair, it’s more than just a catchy tagline or an impressive profile picture; it’s about defining what sets you apart.
What’s your unique niche within cybersecurity? What makes you different from other candidates? Your personal brand should reflect this uniqueness across all your professional interactions.
Creating a cybersecurity portfolio or a professional LinkedIn profile helps you to create a unified brand that resonates in the mind of a cyber security recruiter.
Your social media, your blog, your GitHub – they all tell recruiters who you are.
The consistency, professionalism, and engagement you exhibit in your online presence can be as influential as your skills and certifications.
Building a personal brand isn’t a one-time task; it’s an ongoing process that requires attention and nurturing.
Therefore, the more effort you put into crafting and maintaining your personal brand, the more it’ll catch recruiter’s attention.
Remember, your brand is your calling card; make sure it speaks volumes.
Receiving job offers is thrilling, but it’s also a critical moment where careful evaluation is required.
It’s easy to fixate on the salary, but a fulfilling cybersecurity career involves much more.
Look beyond the numbers to consider the company’s culture, the team dynamics, and the growth opportunities.
Align offers with your long-term goals and values, and don’t be afraid to negotiate.
Negotiation isn’t just about asking for more money; it’s about communicating your value, your expectations, and finding common ground with your potential employer.
Practice negotiation techniques, understand the industry standards, and be prepared to discuss your worth with confidence.
Consider seeking professional guidance or using resources like PayScale or Salary.com to gauge market rates.
If multiple offers come your way, take your time to analyze them, even if it means requesting additional time from the cybersecurity recruiters.
The offers you receive from cyber security recruiters are not merely contracts; they are the starting point of your next chapter in cybersecurity.
Navigate them with care, foresight, and a clear understanding of what you want and need from your career.
Emotional Intelligence and Workplace Culture
When it comes to finding the right fit in a cybersecurity role, emotional intelligence (EI) and cultural alignment are as vital as your technical skills.
Understanding and adapting to a company’s culture isn’t just about getting along; it’s about thriving in that environment.
When cybersecurity recruiters evaluate candidates, they don’t just look at what you know; they look at how you fit within their team and their company’s ethos.
Emotional intelligence – your ability to recognize, understand, and manage both your emotions and those of others – plays a vital role in how you interact with your coworkers and approach your work.

In a CareerBuilder survey, 2,662 U.S. hiring managers were asked:
#1) Why emotional intelligence is more important than high IQ? (In order of importance):
- Employees [with high EI] are more likely to stay calm under pressure
- Employees know how to resolve conflict effectively
- Employees are empathetic to their team members and react accordingly
- Employees lead by example
- Employees tend to make more thoughtful business decisions
#2) What behaviors and qualities are displayed by those with emotional intelligence? The top responses from the survey were:
- They admit and learn from their mistakes
- They can keep emotions in check and have thoughtful discussions on tough issues
- They listen as much or more than they talk
- They take criticism well
- They show grace under pressure
Take the time to research a company’s values, team dynamics, and working style.
During interviews, ask questions that give you insight into their culture and the role.
Share your thoughts on teamwork, leadership, and collaboration to show cybersecurity recruiters how your EI aligns with their needs. That means pay attention and be prepared to ask questions that keep your interviewers on their toes, without being overly critical.
In demonstrating your emotional intelligence and your understanding of their workplace culture, you prove that you’re not just a fit for the role but a match for their team.
Conclusion
Embarking on a cybersecurity career is an exciting, rewarding, and often complex journey. And though the path may seem tangled with various requirements, each step you take shapes your success story.
View these challenges as stepping stones towards your desired role.
Cybersecurity recruiters seek candidates who not only possess the knowledge but demonstrate adaptability, integrity, and alignment with their values.
Therefore, your success isn’t defined by a single skill or achievement. It’s a combination of your experience, your growth, your network, and your ability to resonate with your desired organization.
By the same token, your cybersecurity journey isn’t a destination; it’s an ongoing process, one filled with opportunities to learn, connect, and thrive.
Every challenge, every decision, every connection is a part of your story, a story that’s yours to write.
Videos
Here’s an amazing video presented by Gerald Auger interviewing Joe Hudson, cyber security recruiter and what
Ready to Upload Your Cyber Security Resume?



Great insights! Cybersecurity recruiting firms focus on finding candidates with strong technical expertise and problem-solving skills. They look for professionals who can stay ahead of evolving threats and have a passion for continuous learning. Experience in risk management and certifications like CISSP or CISM are also highly valued in the industry.
Thank you!