“Cyber security domains”; you hear the phrase used all the time, but what does it really mean.
Read on as we attempt to understand how others interpret the cyber security domains versus what might be the best way!
Here are the topic areas we’ll cover in this article:
What Are Domains?
Let’s look at the word “domain.”
A domain is an area of knowledge or set of responsibilities that are in some way related to each other.
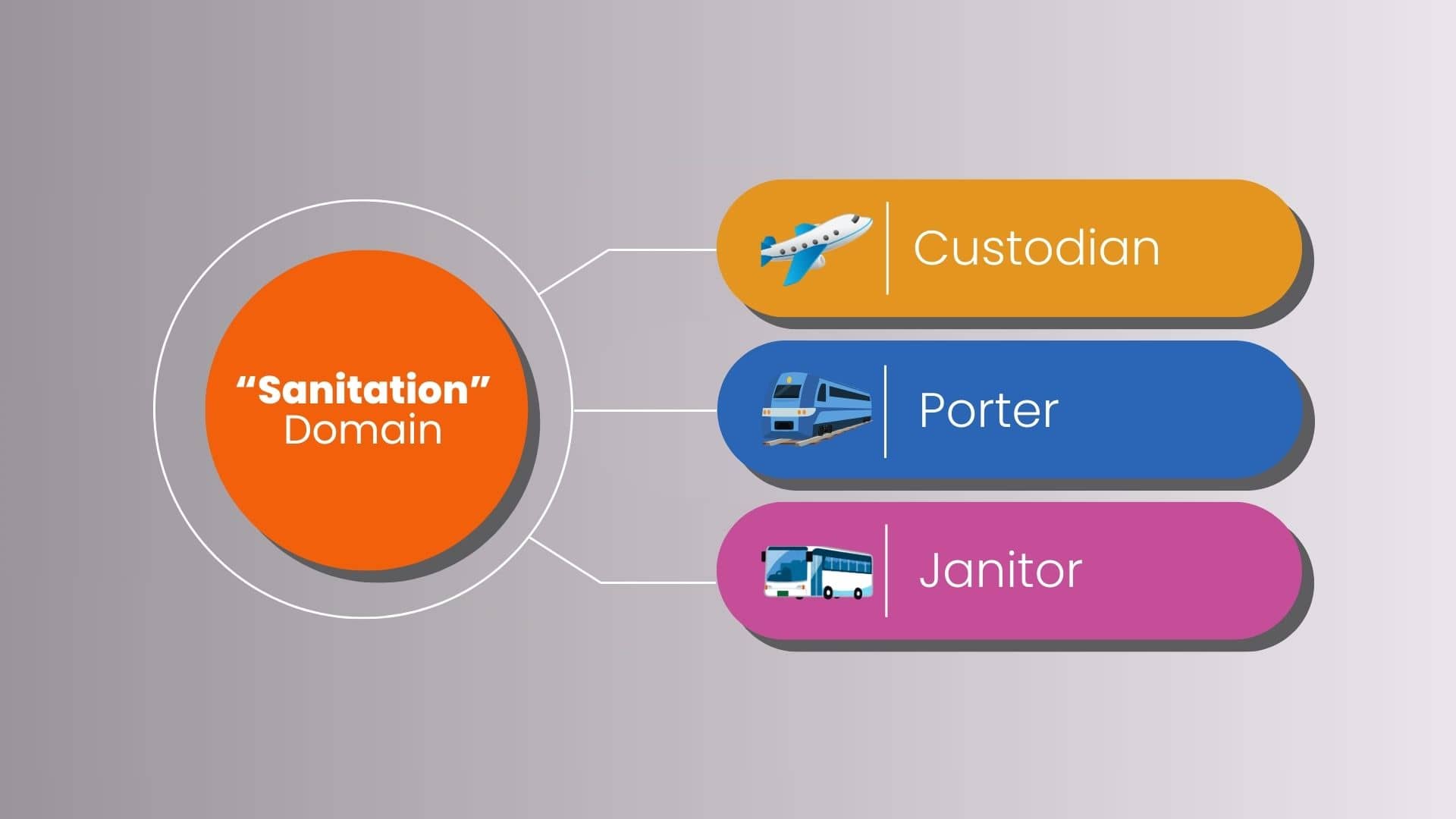
For instance, suppose we’re talking about workers in the transportation industry.
Initially, they might each seem to have very different jobs.
However, many of them have overlapping responsibilities which have nothing to do with job titles.
For instance, a bus cleaner, train porter, and airline custodian all have nearly the same responsibilities.
Yet all three work in the domain of “sanitation”.
Stay with me for a moment…
Why Are “Domains” Important?
Many of us are consciencely aware of what a domain is across different industries.
Regardless of whether someone works in the airline industry, bus industry, or the rail-line industry, a cleaning crew is the pretty much the same across the board.
And the same holds true for many other roles.
If you leave your job in one industry, you might find a similar role in another industry, maybe with some greater responsibility.
However, you don’t go from being a janitor to a pilot on a whim, unless you’re making life-altering decisions.
The point is, that even if your job title changes, your domain (which is somewhat tied to your responsibilities) is likely to remain unchanged.
As a result, it’s easier for others to identify your skillset; in this example, that person might fall under the domain of “Sanitation”. Even though we don’t usually call it that!
What Are Cyber Security Domains?
Cyber security domains are also known by other phrases such as cyber security categories, focus areas, areas of interest, application areas, knowledge areas, specialty areas, areas of study, or areas of expertise. How every you want to say it, they all mean the same thing.
So, when someone talks about cyber security domains, what they really mean is the area of cybersecurity that’s being referenced.
Domains are often associated with governing bodies or cyber security credentialing organizations.
Cyber security is such an immense field that there are many different roles and responsibilities.
And because of its sheer breadth, there had to be a way to categorize all these areas.
For example, there are dozens of different cyber analyst positions.
But does this mean that each has unique responsibilities?
Certainly not! There are several analyst roles that have similar responsibilities or even the same responsibilities, just called by different titles.
It’s the responsibilities that become critical to understand, not the job title.
But the problem is identifying the responsibility of each role.
Fortunately, this is where cyber security domains come into play.
Domains help to group similar responsibilities across different industries and “lump” them together.
Why Are Cyber Security Domains Important?
Because of the vast number of responsibilities even with the same title, it’s difficult to identify someone’s expertise.
So, to ensure roles of security personnel are consistent across industries and companies, you’ve got to identify a set of responsibilities that are common across the cybersecurity field.
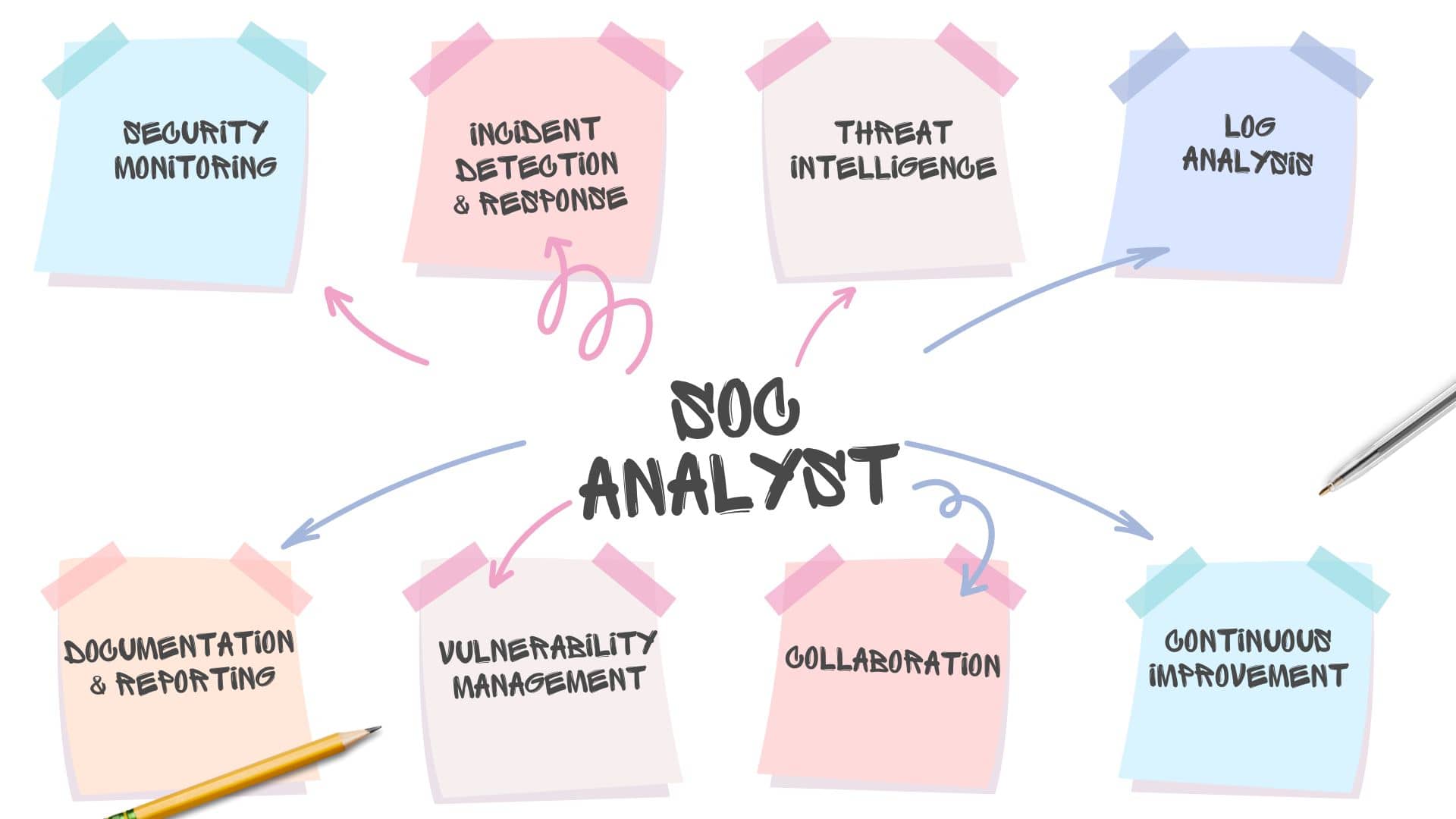
From an HR perspective, cybersecurity domains provide a clear framework for creating accurate job descriptions, identifying the specific skills and qualifications needed for different cybersecurity positions, and guiding recruitment efforts.
How Many Cyber Security Domains Are There?
There’s no easy answer to that question.
Even I was quite surprised to find out that domains aren’t set in stone.
The list of cyber security domains is often organization or agency specific, and no standard definition exists.
The exact number of domains can differ based on the organization’s specific needs and the cybersecurity framework being followed.
Let’s take a look at a few examples.
ISC2 Domains
For certifying organizations such as ISC2, domains help test takers understand what topics an exam will cover.
Certified in Cybersecurity Domains
This entry-level certification provides you with a solid foundation in cybersecurity and perfect if you’re just starting your career in cybersecurity
It covers the basics of network security, application security, and incident response.
The Certified in Cybersecurity exam has five security domains.
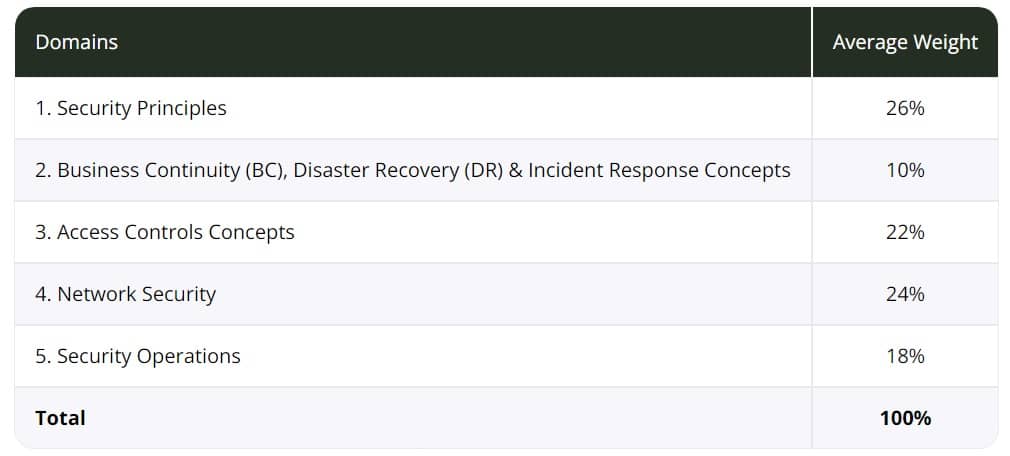
You can see that not ever domain is weighted equally.
Additionally, more focus is given to security principles and network security than the others.
ISACA Domains
ISACA has several certifications related to cyber security; unfortunately, they don’t have any entry level cyber security certifications.
Instead, we’ll take a look at the more popular CISA exam.
CISA Domains
The CISA certification, is a very common security auditing “cert”.
It’s a globally recognized certification that validates expertise in assessing and controlling an organization’s IT and business systems.
It too covers five domains that are very different from the previous certification.
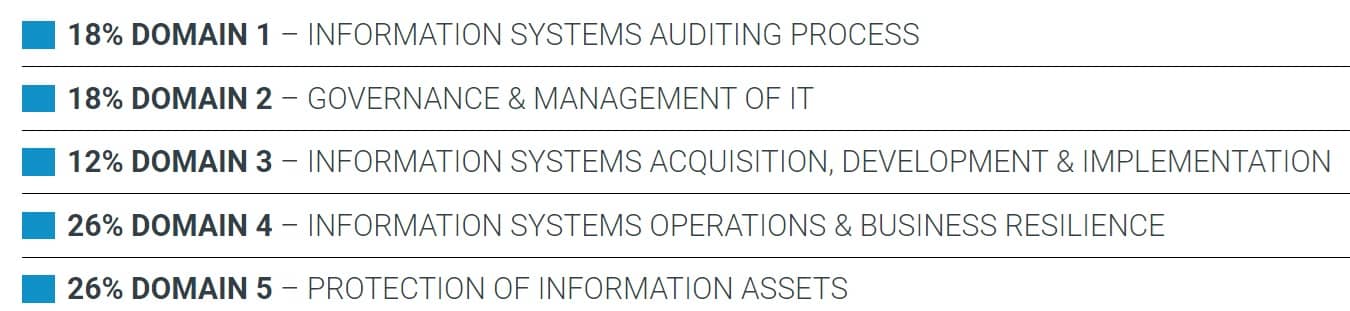
Notice that the domains for the CISA are related to auditing and goes back to what I mentioned about domains being very much organization specific.
BTW, if you’re interested in security auditing, check out my article about becoming a security auditor.
CompTIA Domains
Even one of the most popular security testing organizations for entry-level candidates has its own domain names.
Security+ Domains
The Security+ certification is one of the most popular cyber certifications in the world if you want to enter cybersecurity.

This Security+ is more focused on making you well-prepared for a variety of entry-level cybersecurity roles which is why this exam covers five domains

- General Security Concepts
- Threats, Vulnerabilities & Mitigations
- Security Architecture
- Security Operations
- Security Program Management & Oversight
The domains are intentionally designed to give you a basic, yet broad, coverage of multiple cybersecurity domains.
GIAC Domains
GIAC has so many cyber security certifications, but one of the most popular entry-level certification exams is the GSEC.
GSEC Domains
SANS, creators of the GSEC certification, mention nine GSEC domains.
- Defense in Depth, Access Control, and Password Management
- Cryptography
- Cloud Operations
- Defensible Network Architecture, Networking and Protocols, and Network Security
- Incident Handling and Response, Data Loss Prevention, Mobile Device Security, Vulnerability Scanning and Penetration Testing
- Linux
- SIEM, Critical Controls, and Exploit Mitigation
- Web Communication Security, Virtualization and Cloud Security, and Endpoint Security
- Windows
The domains of the GSEC certification still maintain broad coverage but are more defined than the Security+. That makes sense because the GSEC is a more advanced certification than the Sec+, going beyond just basic concepts.
As you can see, different certifying organizations categorize cyber security domains according to the topics covered in their certification exams.
Cybersecurity Domains for Organizations
Domains aren’t always classified by certifications, even organizations use domains to classify roles.
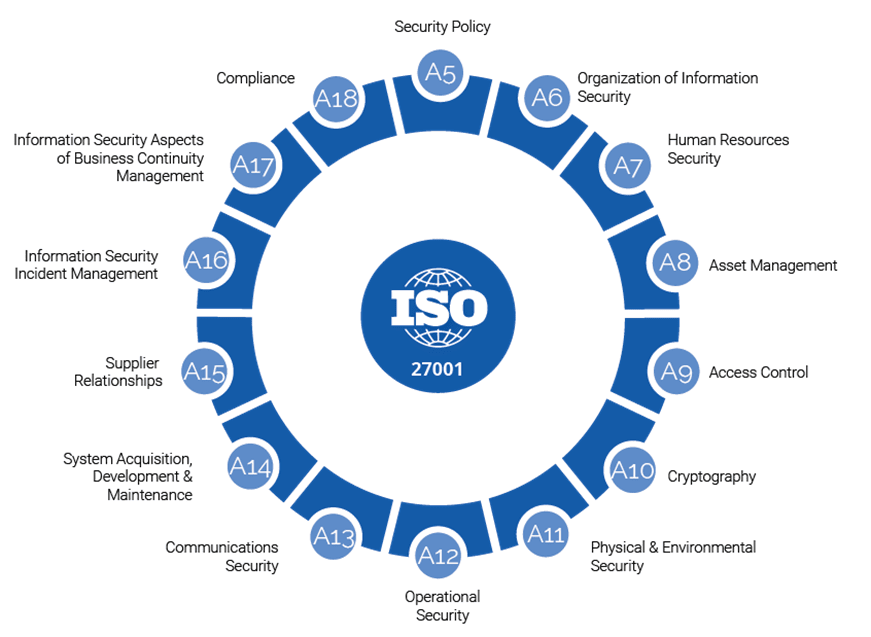
For example, ISO/IEC 27001 includes 14 domains within its information security management system (ISMS) framework.
The US Department of Energy, which helped to develop the Cybersecurity Capability Maturity Model (C2M2), has decided upon the following 10 domains:
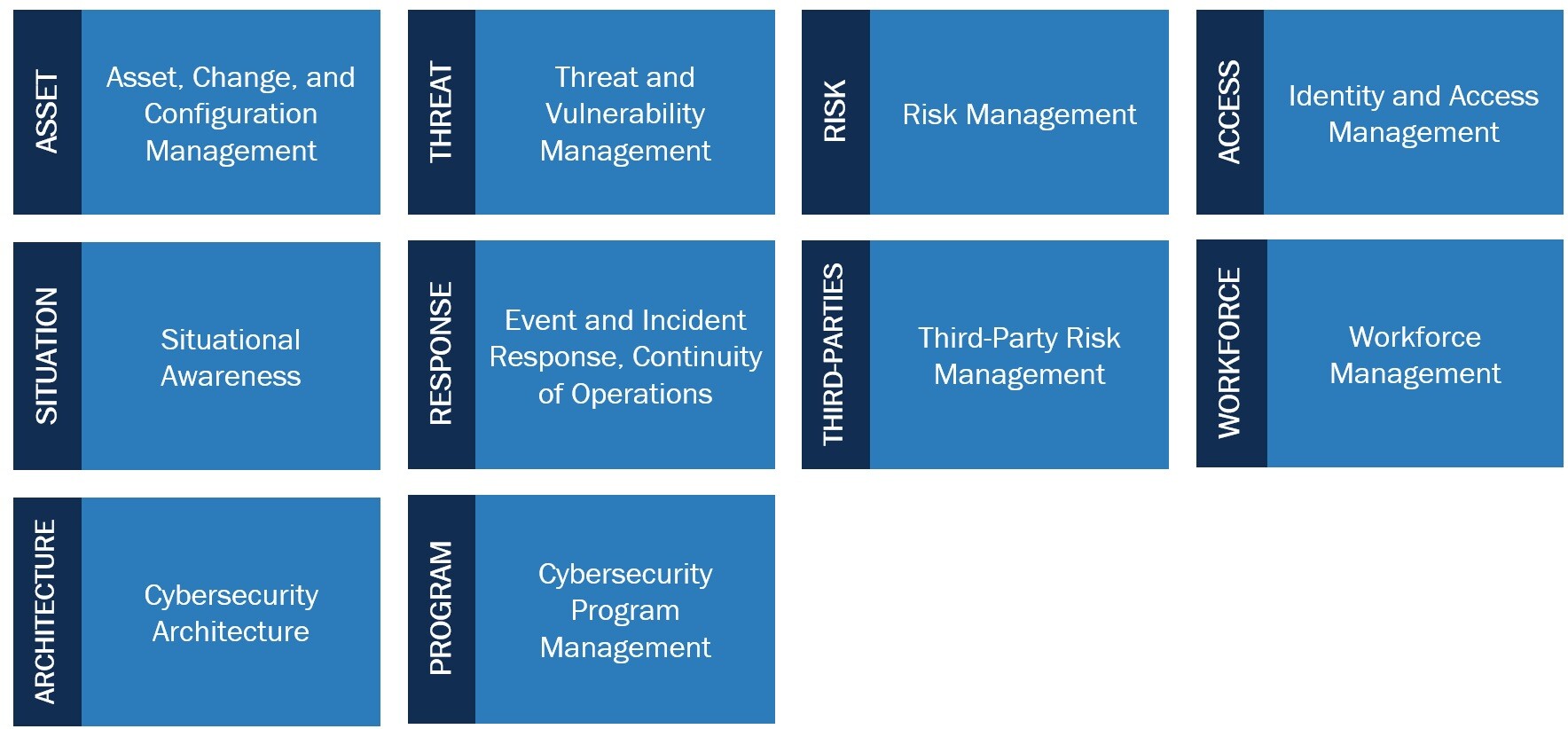
- Asset, Change, and Configuration Management (ASSET)
- Threat and Vulnerability Management (THREAT)
- Risk Management (RISK)
- Identity and Access Management (ASSESS)
- Situational Awareness (SITUATION)
- Event and Incident Response, Continuity of Operations (RESPONSE)
- Third-Party Risk Management (THIRD-PARTIES)
- Workforce Management (WORKFORCE)
- Cybersecurity Architecture (ARCHITECTURE)
- Cybersecurity Program Management (PROGRAM)
Surprisingly, even the NIST Cybersecurity Framework (CSF) covers the following six domains which are the most simplified:
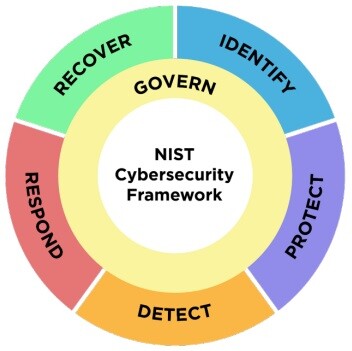
- Govern
- Identify
- Protect
- Detect
- Respond
- Recover
The list goes on, but I hope you’re starting to get the point.
Is There an “Official” Cyber Security Domain?
There will probably never be a single, agreed-upon standard for cybersecurity domains because cybersecurity is constantly changing.
Different industries and organizations have unique security needs and risks, which means they prioritize different areas.
Plus, there are many frameworks and regulations that define cybersecurity differently, and new technologies keep introducing new challenges.
This makes it hard to create one standard that fits everyone’s needs and approaches.
That doesn’t mean people aren’t trying!
What Are the 11 Domains of Cyber Security?
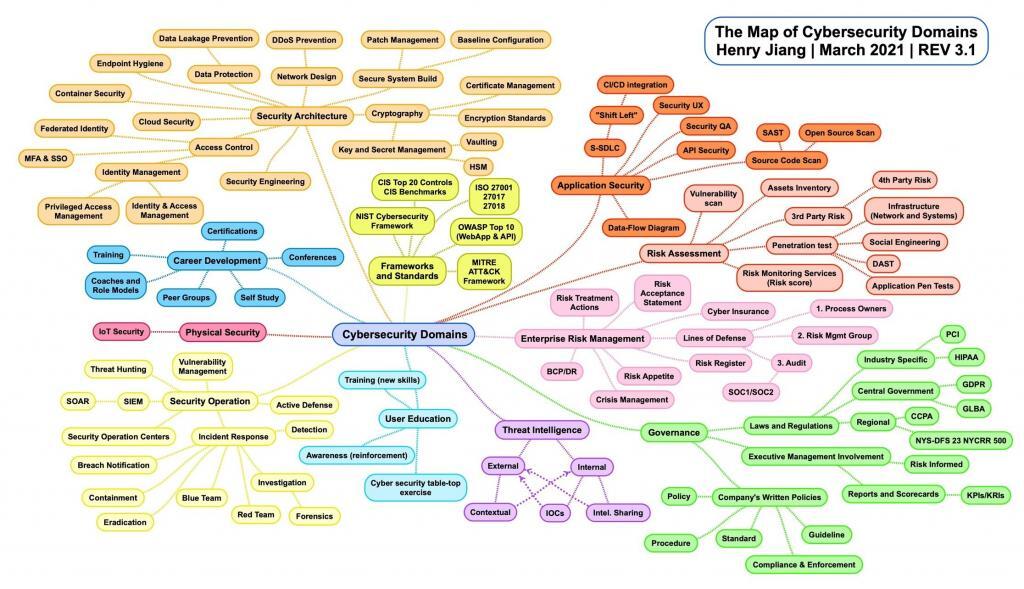
Let’s look at another popular example by Henry Jiang, creator of The Map of Cybersecurity Domains v3.1 and the most vendor neutral of all the examples. His model lists 11 cyber security domains:
- Frameworks and Standards
- Application Security
- Risk Assessment
- Enterprise Risk Management
- Governance
- Threat Intelligence
- User Education
- Security Operations
- Physical Security
- Career Development
- Security Architecture
And though you may not agree, it does do a better job of capturing a more holistic view of cyber security. A brief description of the 11 domains along with the Tier-1 subdomains are referenced below.
1. Frameworks and Standards
Frameworks are important because they provide a common template from which all others can follow.
They help ensure that security teams are able to follow a structured path towards achieving security.
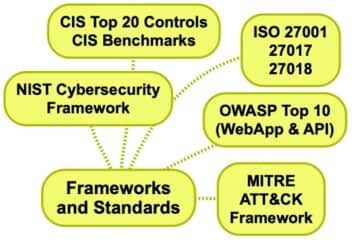
- NIST Cybersecurity Framework
- CIS Top 20 Controls / CIS Benchmarks
- ISO 27001 / 27017 / 27018
- OWASP Top 10
- MITRE ATT&CK Framework
2. Application Security
Application security is the practice of protecting the software applications from security threats and vulnerabilities.
By integrating security measures into every stage of the application’s lifecycle, from design to deployment, apps are more safe, reliable, and trustworthy for everyone who depends on them.
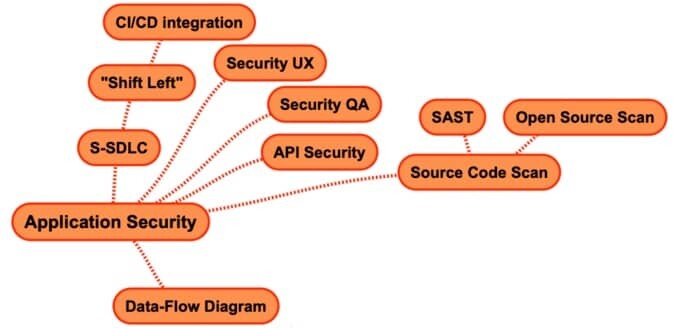
- S-SDLC
- Security UX
- Security QA
- API Security
- Source Code Scan
- Data-Flow Diagram
3. Risk Assessment
Risk assessment is the process of identifying threats and vulnerabilities to an organization and its assets, then assessing the likelihood and impact of these threats to the organization.
The assessment is used to determine what security controls are necessary to mitigate the impacts of a potential security incident.
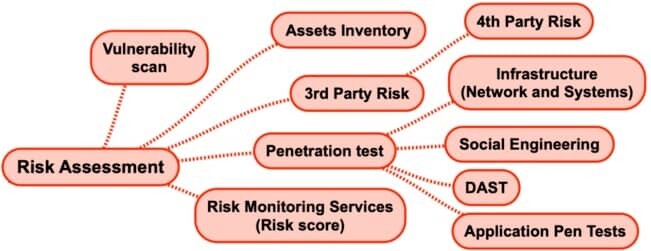
- Vulnerability Scan
- Assets Inventory
- 3rd Park Risk
- Penetration Test
- Risk Monitoring Services
4. Enterprise Risk Management
Enterprise Risk Management (ERM) is a method organizations use to identify and deal with potential problems (aka risks) that could affect their success.
It involves everyone working together to spot risks early and find ways to manage them, so the company can achieve its goals without unexpected setbacks.
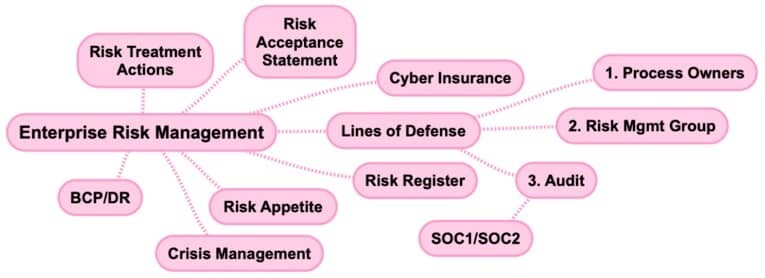
- Risk Treatment Actions
- Risk Acceptance Statement
- Cyber Insurance
- Lines of Defense
- Risk Register
- Risk Appetite
- Crisis Management
- BCP/DR
5. Governance
Security governance is the way an organization directs and controls its efforts to keep information and assets safe.
It involves setting clear policies and procedures so everyone knows their roles in maintaining security.
By doing this, the organization ensures that its security practices support its goals and comply with laws and regulations, while effectively managing risks and protecting stakeholder interests.
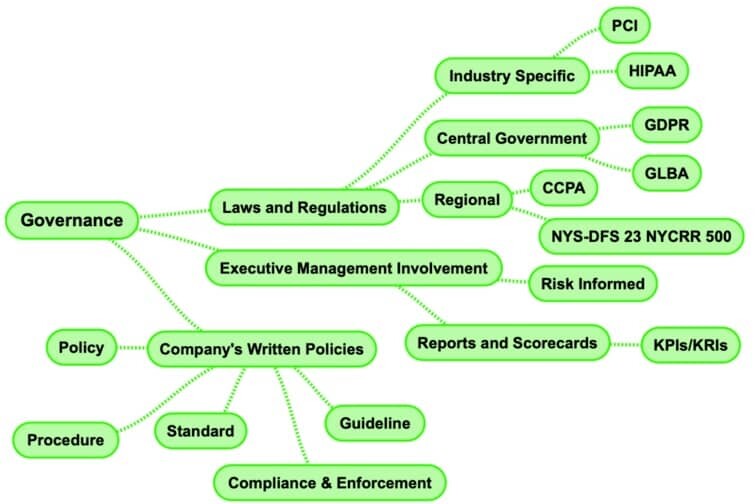
- Laws and Regulations
- Executive Management Involvement
- Company Written Policy
6. Threat Intelligence
Threat intelligence is the process of collecting and analyzing data about cyber threats.
Used in conjunction with other cybersecurity solutions, threat intelligence can be used to protect against cyber-attacks.
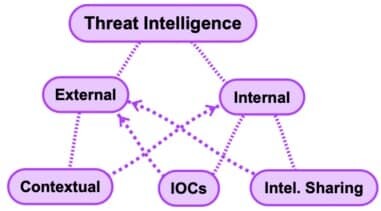
- External
- Internal
7. User Education
Another key element of the cyber security domains is user education.
It’s a part of the security lifecycle, and it’s all about getting people to understand the importance of security.
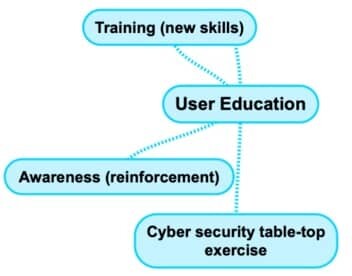
- Training
- Awareness
- Cyber Security Table-Top Exercises
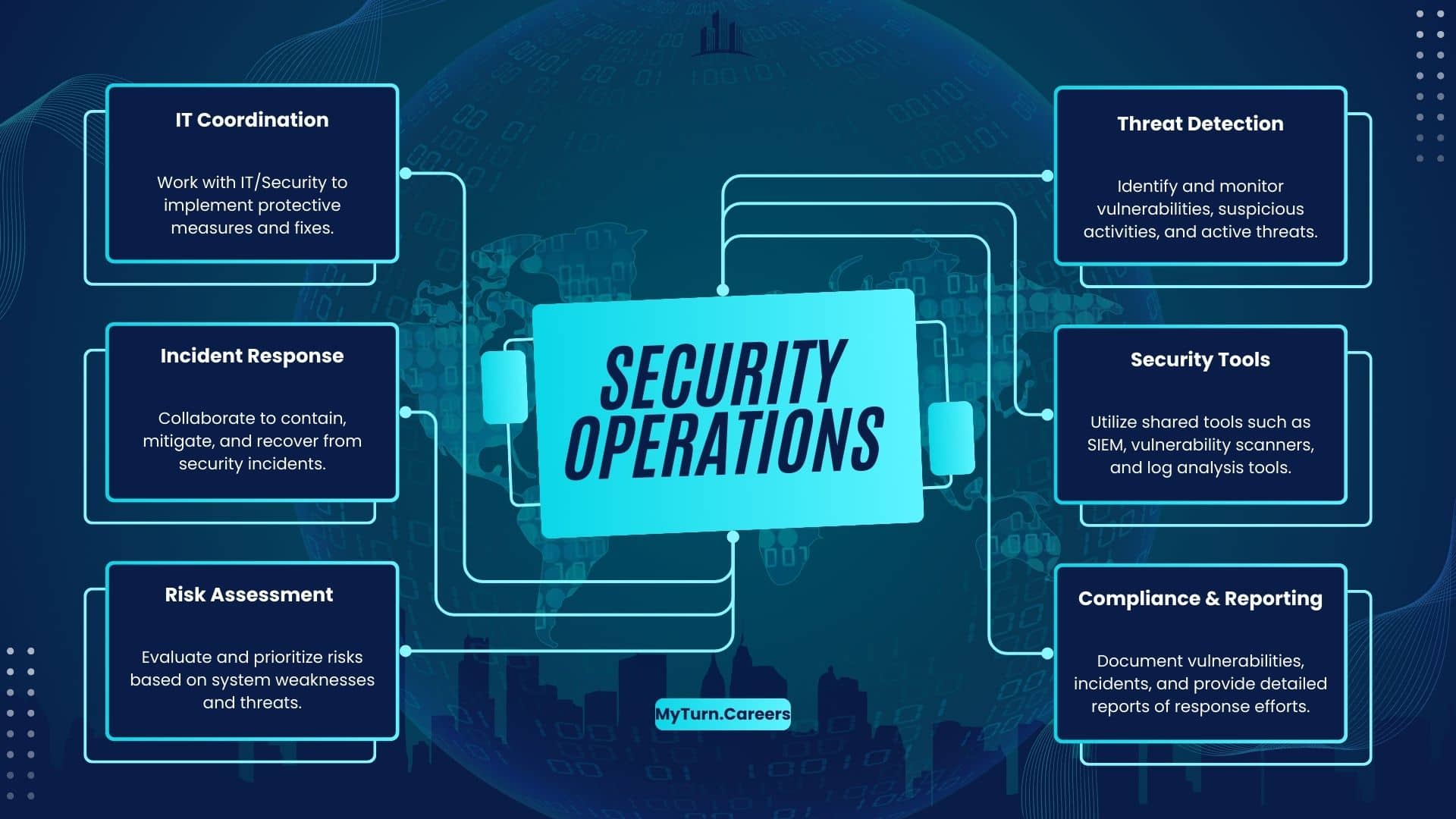
8. Security Operation
Security operations is the team that keeps systems running and secure, monitoring them for incidents and responding to them when necessary.
They also update security processes and policies as needed, ensuring that all the technology is up-to-date and working properly.
Security operations personnel are responsible for knowing all aspects of their organization’s cybersecurity program—from policy to technology—so they can respond quickly when an attack occurs, or a vulnerability must be patched.
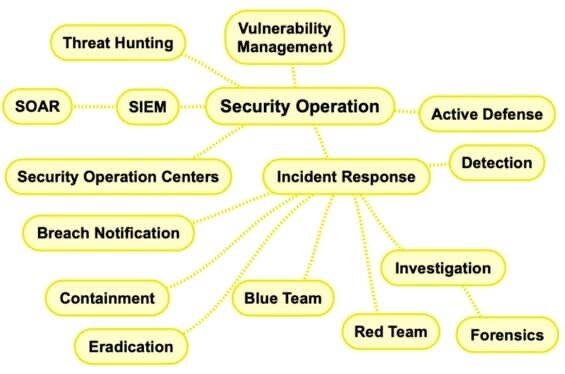
- Vulnerability Management
- Active Defense
- Incident Response
- Security Operation Centers
- SIEM
- Threat Hunting
9. Physical Security
Physical security is a broad category that includes all measures of preventing any unauthorized access to people or property.

- IoT Security
10. Career Development
As strange as it may sound, career development has also been included as a cyber security domain.
The intense demand of qualified cyber security professionals requiring a good education, skills and experience makes this domain an invaluable asset to the industry.
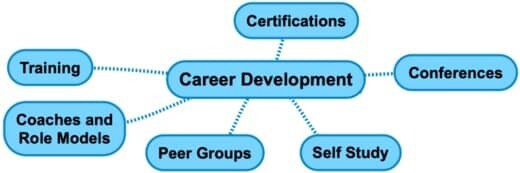
- Certifications
- Conferences
- Self-Study
- Peer Groups
- Coaches and Role Models
- Training
11. Security Architecture
Security architecture is the design of the security policy and strategy of an organization and is quite broad in scope.
These are all security-related categories that must be addressed when designing your application’s architecture.
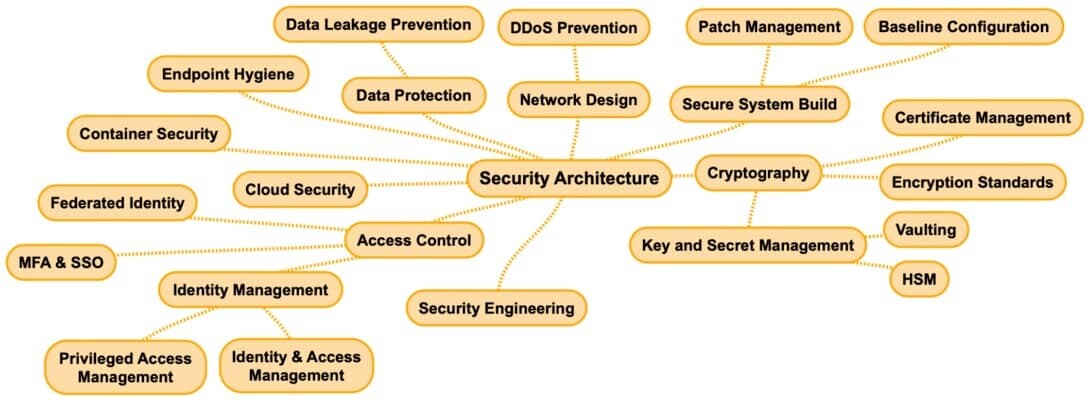
- Network Design
- Secure System Build
- Cryptography
- Security Engineering
- Access Control
- Cloud Security
- Container Security
- Endpoint Hygiene
- Data Protection
Cybersecurity Domains: The Big Picture
When all the cybersecurity domains are brought together in this layout.
What Are the 8 Domains of Cybersecurity?
It’s common to hear about the eight domains of cybersecurity.
Anytime you hear that, what’s really being discussed are the 8 domains of CISSP certification.
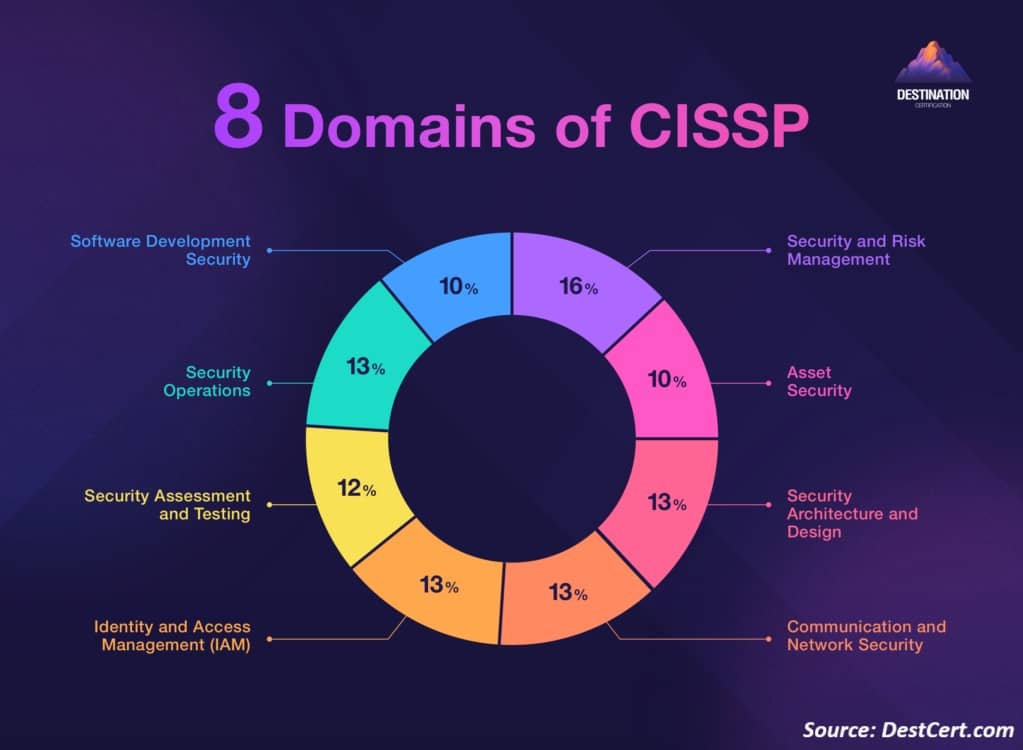
- Security and Risk Management
- Asset Security
- Security Architecture and Engineering
- Communication and Network Security
- Identity and Access Management (IAM)
- Security Assessment and Testing
- Security Operations
- Software Development Security
As I mentioned previously, this has more to do with the CISSP exam than anything else.
So, the next time you hear anyone speaking about cyber security domains, just make sure you understand the context behind the discussion.
Looking to upgrade your career?
View our listing of cybersecurity jobs!
Interested in More…
Cyber Security vs Information Security?
Why Take the Security+ Certification?
Ways to Work in Cyber Security Without a Degree!